Add your own sensitive info types to use in sensitivity labels
As you probably know Microsoft has provided us with a list of predefined sensitivity types that follows us around wherever we can configure labels etc. It is getting better and better as more types are added, but we may not find all the types we would need for a setup, and that's why I want to show you how you can add your own sensitivity types.
For those of you familiar with the Office 365 Security portal (https://security.microsoft.com), you will have noticed the Classifications menu.
If you look at Sensitive info types, you will see a wide range of predefined types, including Credit Card info, and a lot of country specific info types.
But you may want to create your own, and Microsoft has made that pretty easy in the new Security center although we can see some signs that it is not all finished. We will have to go to the Security & Compliance Center to do this:
Here we can select Sensitive info types and choose to Create a new info type.
We will give it a name and description
We need to add some requirements for matching. This is the sensitive info that our new type will look for in a document very much in the same way as the "Credit Card Number" info type will look for a Credit card number in the content. We can enter several keywords separated by comma. If we want to add a string, we can do this as well, in double quotes.
To increase the accuracy of detection, we can choose to add one or more supporting elements. I choose to have a minimum keyword count of 2. (based on earlier experiences) which means that my Keyword will have to appear twice in the content before it matches this Sensitive info type.
I will leave the confidence level at 60% which is the default. This defines the match confidence of the pattern. You may want to change this to something higher if you are afraid of false positives. In our case we choose to also keep the default character proximity of 300. This means that when the first pattern element is matched, any supporting elements will match only when found inside this proximity of the first element.
When we have gone through this, we will have a chance to review our settings again before selecting finish. A pretty cool test possibility allows us to test our new info type by dragging and dropping a document containing something that will trigger the type.
I create a word document and put some of the words we defined earlier into it.
I then drag and drop it to see what happens
I choose to Test and see that we got matches.
How do we use our new Sensitive info type?
Okay, so we have created a new sensitive info type, and want to use it for one of our labels. We go to labels, and under Sensitivity we choose to Create a label. Our new label Wizard will guide us through the label configuration, starting by asking us to give the label a name, a Tooltip text, (which is what appears if we let the mouse hover over the label) and a description which is for admin/internal use.
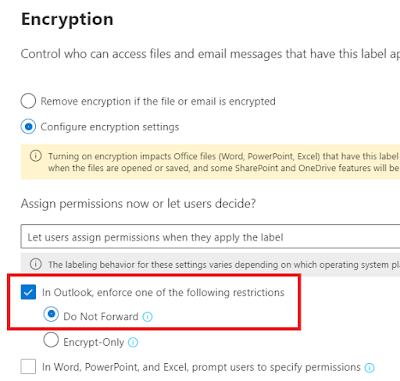
In our case we want our label to provide Encryption, and we will grant permissions to us this label/read the information protected by this label to all the users in our tenant. We can choose different kinds of permissions from Viewer to Co-Owner, and we can even use custom permissions here, but for this guide, we will choose Co-Author, which means all the users in our tenant will have every right except the right to remove the encryption someone else has set to the content (You have Co-Owner to the content you have protected yourself.) Since we are going to add Auto labelling for this label, and this is an E5 (or equivalent) function, you may want to specify only a subset of users that has E5 license.
Now on to the visual markings. Depending on what kind of label this is you may want to have a header/footer or even a watermark. We choose watermark, and specify Internal Information.
We leave the rest as is and move on to Endpoint data loss prevention and also leave this as is.
Now we come to one of the options that require an E5 license (or equivalent). Auto labeling. This function also requires you to install the Azure Information Protection unified labeling client. Under Detect content that contains, under default we will select add and then Sensitive info types. Since we have a lot of predefined ones, we will type in intern to find the sensitive info type we created. We select this, and under When content matches these conditions, we will choose between recommend user to apply the label or we can choose to Automatically apply the label. For this we will choose to Automatically apply the label.
We now have a label that is using our new sensitive info type, but it will not yet be available for our users. To do this we need to publish the label. In the same place where we started to create our new label, we choose the Publish labels options. Here we see that the list is currently empty, so we select Choose labels to publish.
This will open the Choose labels pane. This will also be empty, so we choose + Add.
This will bring up a list of all available labels. We find our Internal-Info label, and select it.
As we can see here, 1 label is added.
Now we have another chance to limit the scope for this label. In our case we will select all Users and groups.
Do we want our users to provide justification if they remove the label or lower the classification? Yes indeed we do. We can also require users to apply a label for all mail and documents, but this can get annoying fast, so be careful with that.
And we need to give our new policy a name and description.
If you are still reading, it is time to see the fruits of our labour. We have created a new Sensitive info type, we have created a new label that is autoprotecting content based on our new Sensitive info type, and we have published the label. We go to a client that has installed the Azure Information Protection unified labeling client, and see that our new Internal-Info label is there in the list of labels.
We test to see that the automatic labeling rule is working. Remember that we used the words Sensitive or Confidential, and that the word would have to be used twice for the rule to auto label content. As you can see below our word document gets automatically labeled as Internal-Info.
So, there you go. We have tested our new Sensitive info type, and created a label that used this and published it to our users. Hopefully you can play around with this a little, and in my experience it is important to be very sure about using automatic labeling rules by keywords. I would prefer to set up automatic recommendation first, and see how this works.






























Comments
Post a Comment